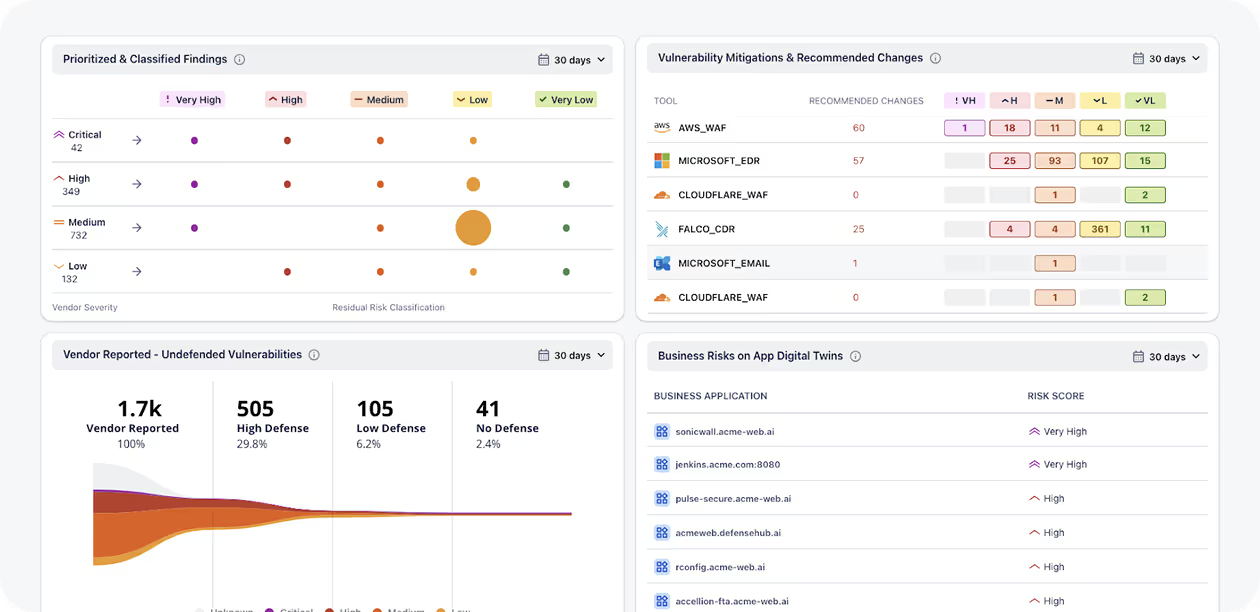
Prove What’s Exploitable. Fix What Matters.
Preemptive, AI-driven security operations that simulate real attacks, validate defenses, and continuously close exploitable paths.
























Fragmented Vendors.
Overloaded Analysts.
Missed Threats.
Each security tool sees only a slice of the problem, slowing response, and leaving analysts to piece together the context by hand.
Siloed tools
SIEM, EDR, IAM, CSPM, WAF, all blind to each other.
Overwhelming alerts
Alerts can be filtered before Tier 1 with the right signal intelligence
Vulnerability backlog
100k+ unpatched exposures in the average enterprise.
The building blocks of preemptive defense
Security Mesh Integration
All your SIEM, EDR, CSPM, IAM, WAF, and cloud data normalized into one semantic layer.
Live Digital Twin Simulation
A live model of your environment showing how real threats could move today
AI Analysts for Each Tier
Role-based AI analysts that cut false positives and automate Tier 1–3 tasks
Closed-Loop Feedback
Every action feeds back into the system, making controls smarter with each signal.
24/7 Threat Coverage
Always-on analysis, validation, and response without missed shifts or escalation delays..
From Telemetry to Preemptive Defense
Ingest and Normalize
Tuskira connects to your SIEM, EDR, CSPM, IAM, GRC, and more. Ingesting and normalizing telemetry into a unified model. We cover over 150 integrations
Outcome: A continuously updating semantic layer of your environment.
.avif)
.avif)
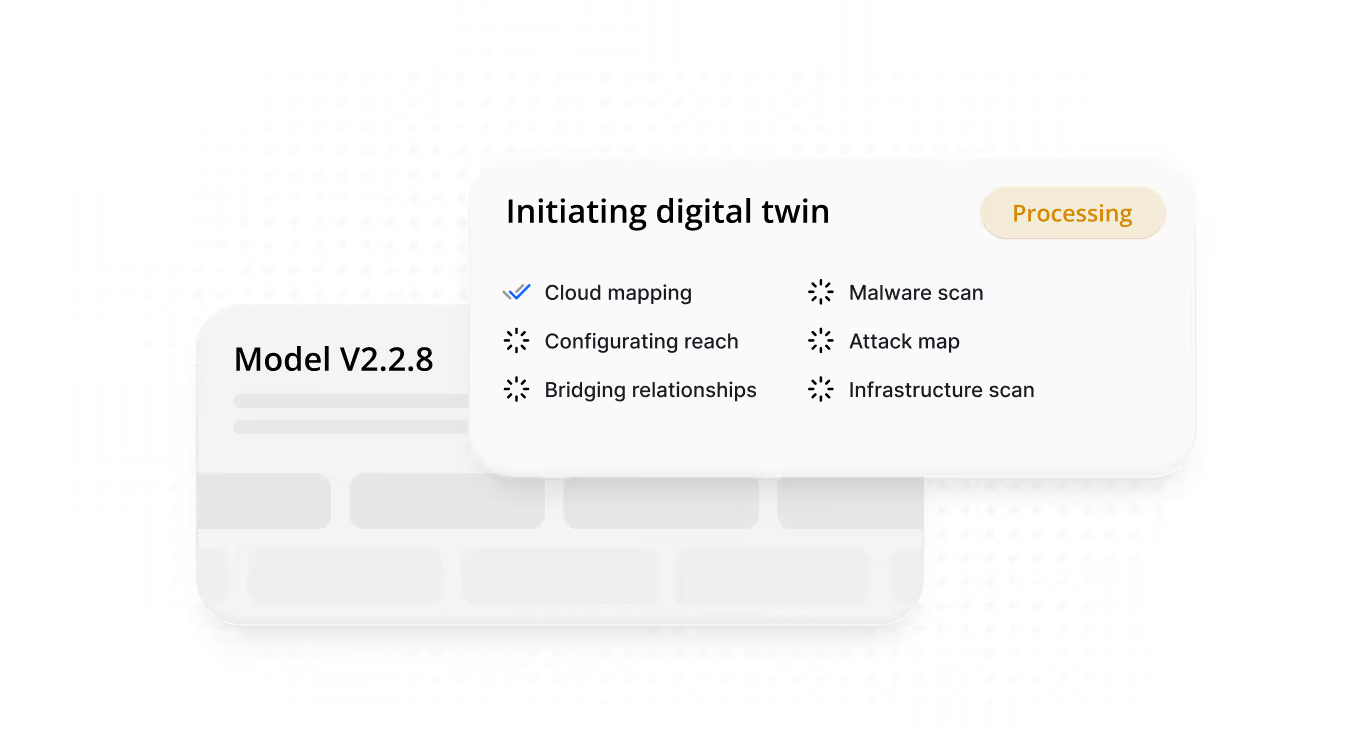
Build the Digital Twin
We map cloud configs, identities, network reachability, and controls into a live model.
Outcome: Full visibility into how attackers could move through your environment today.
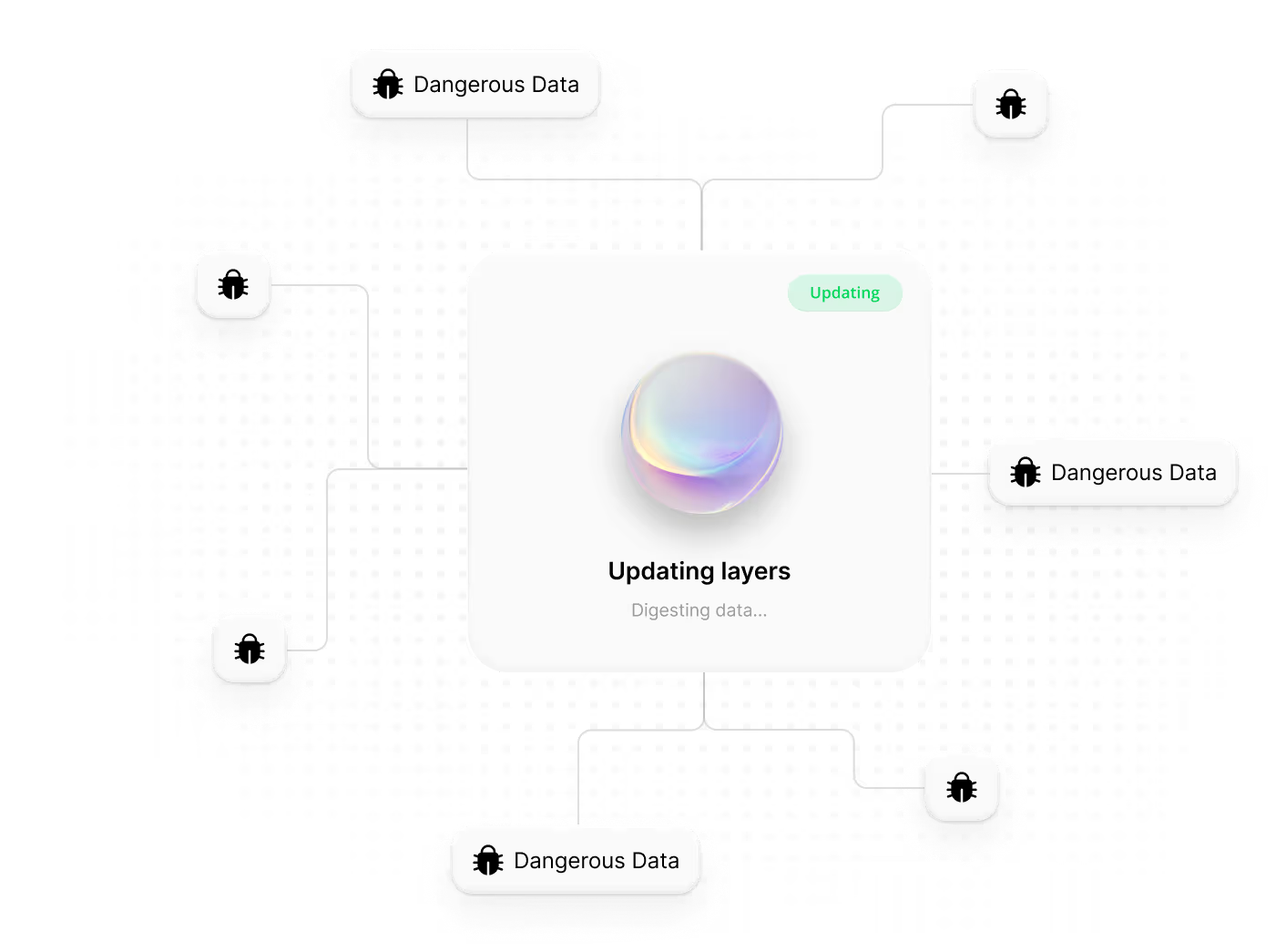
AI Simulation & Validation
Attack paths are continuously tested against your defenses behind the scenes to see what’s truly exploitable.
Outcome: False positives are filtered out, and risks are prioritized based on the real reachability of the attacker.
.avif)
.avif)

AI Analysts Act
Role-based Analysts (Vulnerability, Zero-Day, Threat Advisory, Remediation) triage alerts, correlate context, and automatically tune defenses.
Outcome: Faster MTTR, reduced manual workload, and automated Tier 1–3 coverage.
Closed loop defense
Every simulation, analyst action, and posture drift feeds back into the mesh.
Outcome: Autonomous defense that adapts over time, getting better with every signal.
.avif)

Validate Threats
Accelerate Mitigation
Measurable ROI
Prove which threats matter with business context, so every fix cuts real risk and drives measurable ROI.
.avif)
.avif)
98% less
Alert noise, our AI filters noise before it hits tier 1.
60% less
Attack paths, live simulations surface and shut down exposures.
5-minute
Triage time, validated threats, routed with full context.
Maximize your tools
Achieve a measurable ROI
From Signal Overload to Strategic Execution
Continuous Defense Validation
Control testing, closed-loop learning.
Threat Exposure Management
CTEM, vuln validation, attack surface simulation.
Autonomous Operations
AI Analyst workforce, response orchestration.
DevSecOps + Compliance
Code-to-cloud security, GRC automation.
What security leaders are saying
Stop reacting. Start preempting.
Book a Demo to see how AI Analysts validate threats, close attack paths, and keep you ahead of risk.

Watch the video
Learn how Tuskira transforms noisy SOCs into autonomous, AI-driven defense systems that validate, simulate, and preempt threats.

